Enable or Disable Dataprep
Dataprep by Trifacta is a third-party service integrated with Google Cloud Platform. This section describes the requirements for enabling the product and how to disable it in your projects if needed.
Enable Dataprep
After it is authorized, Dataprep by Trifacta only accesses project data when permitted by the user in the following ways:
Browse and preview project data
Read project data into Dataprep by Trifacta for transformation purposes
Write results of jobs back to the project
Attach service accounts in your project to Dataflow jobs used for transformation.
All project data is read from and written to user-owned projects.
Note
No BigQuery or Cloud Storage data is stored by Dataprep by Trifacta or by Alteryx.
Cloud Storage bucket
When Dataprep by Trifacta is enabled in your project, Google creates a Cloud Storage bucket for you. Your project is automatically provisioned to use this bucket.
Note
This bucket is created by Google and is not under the control of Alteryx. It is associated with a specific project.
Note
This bucket is created in a region within the United States.
During enablement in the project, you may receive aFailed: Create bucketerror. If your enterprise permissions do not permit the creation of a bucket in the United States, then please create a bucket with the following naming convention:
dataprep-staging-<yourDesignation>
The designation information can be any accepted value.
Enable per Project
Access is created and enabled on a per-project basis.
Steps:
Access a project where you are the project owner.
In the Google Cloud Console, navigate to the product: https://console.cloud.google.com/dataprep.
The project owner must authorize Google to share certain customer information with Alteryx:
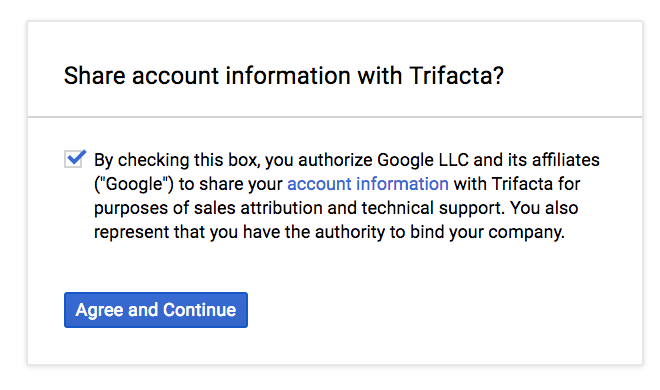
Figure: Share account information
Click Agree and Continue.
Access to project data
The project owner must also enable Dataprep by Trifacta access to project data:
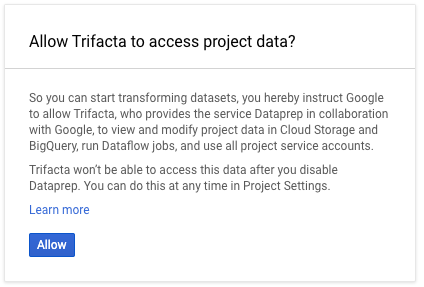 |
Figure: Allow access to project data
Click Allow.
Restricted domains
Google Cloud Platform supports the restriction of domains that have access to cloud resources. The domain restriction constraint is based on the list of constraints in the following setting:
iam.allowedPolicyMemberDomains
Note
If you have enabled restricted domains in your Google organization, you must enable the trifacta.com workspace identifier in the constraints list.
The following example organization policy includes the Google Workspace ID for Dataprep by Trifacta, which is C03k2thv1.
resource: "organizations/12345"
policy {
constraint: "constraints/iam.allowedPolicyMemberDomains"
etag: "\a\005X\352\124\321\811\495"
list_policy {
allowed_values: "C03k2thv1"
}
}For more information, https://cloud.google.com/resource-manager/docs/organization-policy/restricting-domains.
Dataprep service and roles
To enable access, Google Cloud Console creates a service account that belongs to the Dataprep by Trifacta service and supplies it with read/write access to Dataflow, Cloud Storage, and BigQuery in the Google Cloud project. For more information, see Dataprep Roles→dataprep.serviceAgent.
Warning
IAM service accounts. The roles/dataprep.serviceAgent role that is granted during product activation includes the roles/iam.serviceAccountUser role. This role enables access to all service accounts in the project, including service accounts that may be created in the future.
For more information, see Required Dataprep User Permissions.
Launch Dataprep
After the project owner has enabled Dataprep by Trifacta for a project, users who are granted the roles/dataprep.user role for the project can access the product.
When a user launches the product in a project for the first time, the user must complete the following:
Log in to a Google account.
Accept the Terms of Service.
Choose a Cloud Storage bucket to use with the product.
For each project to which you have access, these steps must be performed the first time that you access the product.
Disable Dataprep
Warning
Disabling Dataprep by Trifacta is not reversible. You cannot undo this operation.
Disabling services used by triggers the removal of all Dataflow assets from the product.
All Alteryx metadata is permanently deleted and cannot be retrieved.
Services used by include (and not limited to) Dataflow and Compute Engine.
Disable Dataprep for a project
When Dataprep by Trifacta is disabled in a project, it is disabled for all users in a project. If a project owner disables Dataprep by Trifacta:
Each project user retains access to data (including transformed data) stored within user-owned Google Cloud projects (for example, raw or transformed data stored in Cloud Storage or BigQuery).
Dataprep by Trifacta can no longer access project data, and users can no longer view or transform project data through the product.
All metadata associated with the product is queued for purging in 30 days.
Within this 30-day window, Dataprep by Trifacta can be restored for use with the project by the project owner.
For more information on this process, see Wipe Out Dataprep Data.
Note
If you have provided Dataprep by Trifacta with access to datasets or resources outside of the current project, disabling the product does not remove those permissions. Those permissions must be removed manually. For more information, see https://cloud.google.com/dataprep/docs/concepts/cross-bq-datasets#removing_service_account_access_to_a_bigquery_dataset.
Note
When you disable the product in your project, the Cloud Storage bucket associated with the product is untouched. That data remains.
In the menu in the Trifacta Application, select User menu > Admin console > Settings. For more information, see Dataprep Project Settings Page.
In the Project Settings page, click Disable Dataprep.
This link redirects you to the Google Console.
In the Google Console URL, verify that the project for which you wish to disable Dataprep by Trifacta is selected.
You can navigate to the following location: https://console.cloud.google.com/dataprep/revokeAccess
The following dialog is displayed:
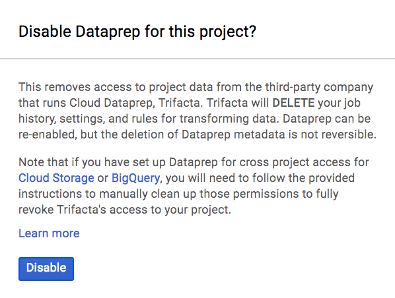
Figure: Disable Dataprep in this project
To disable use of Dataprep by Trifacta in the selected project, click Disable.
The product is disabled for your project.
Restore Dataprep by Trifacta in project where it was disabled:
Note
After Dataprep by Trifacta has been disabled in your project, the Alteryx data in the project is marked for purging. This data is retained for a period of time before it is permanently removed. For more information on purging and restoring data, see Wipe Out Dataprep Data.
Disable billing in Marketplace
If you are no longer using the Dataprep by Trifacta at all, you must disable it through the Marketplace.
Warning
You will continue to be billed for the Dataprep by Trifacta Service according to the terms of your contract until the Service is disabled in the Marketplace.
For more information, see https://console.cloud.google.com/marketplace/product/endpoints/cloud-dataprep-editions-v2.
Forced Cancellations
Some changes to the billing for your project have been known to cause cancellations of Dataprep by Trifacta in your project. These cancellations are submitted from Google, Inc. to Alteryx without additional information.
Note
If you have received an unexpected cancellation of Dataprep by Trifacta for a project, please contact Google Support.
Typically, the solution is to re-enable the product for your project.